A group of academics has revealed information about more than 100 security vulnerabilities affecting LTE and 5G systems that could be exploited by attackers to disrupt service access and potentially infiltrate the cellular core network.
The 119 vulnerabilities, which have been assigned 97 unique CVE identifiers, cover seven LTE implementations – Open5GS, Magma, OpenAirInterface, Athonet, SD-Core, NextEPC, and srsRAN – as well as three 5G implementations – Open5GS, Magma, and OpenAirInterface, according to researchers from the University of Florida and North Carolina State University.
These findings are presented in a study titled “RANsacked: A Domain-Informed Approach for Fuzzing LTE and 5G RAN-Core Interfaces.”
“Each of the more than 100 vulnerabilities discussed below can be exploited to disrupt all cellular communications (including phone calls, messaging, and data) on a city-wide scale,” the researchers stated. “
An attacker can repeatedly crash the Mobility Management Entity (MME) or Access and Mobility Management Function (AMF) in an LTE/5G network by simply sending a small data packet over the network as an unauthenticated user (no SIM card needed).”
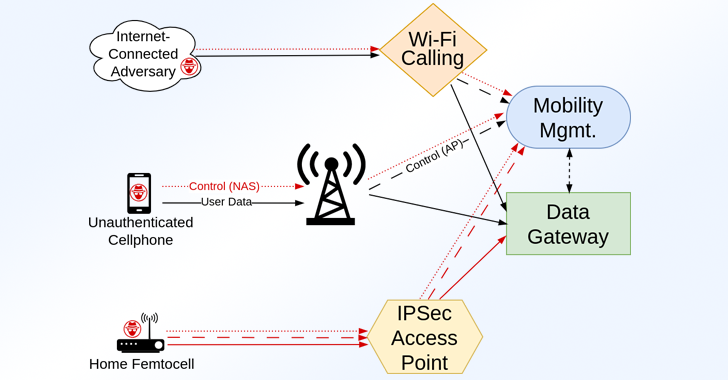
The discovery stems from a fuzzing exercise called RANsacked, conducted by researchers on Radio Access Network (RAN)-Core interfaces that can receive input directly from mobile handsets and base stations.
According to the researchers, several of the vulnerabilities they found are related to buffer overflows and memory corruption errors. These issues could potentially be exploited to breach the cellular core network, allowing unauthorized access to monitor cellphone location and connection information for all subscribers across a city, execute targeted attacks on specific users, and carry out additional malicious activities on the network itself.
Additionally, the identified vulnerabilities can be categorized into two main types: those that can be exploited by any unauthenticated mobile device and those that can be targeted by an adversary who has already compromised a base station or a femtocell.
Of the 119 vulnerabilities discovered, 79 were identified in MME implementations, 36 in AMF implementations, and four in SGW implementations. Twenty-five of these vulnerabilities could lead to Non-Access Stratum (NAS) pre-authentication attacks that can be executed by any arbitrary cellphone.
The study highlighted that “the introduction of home-use femtocells, along with the more accessible gNodeB base stations in 5G deployments, marks a significant change in security dynamics: where RAN equipment was once physically secured, it is now vulnerable to physical adversarial threats.”
Additionally, the research discusses the implications of this final area by enabling effective fuzzing interfaces that were previously assumed to be secure but are now facing immediate threats.