“New Trojan Threat: Quasar RAT Disguised as Ethereum Security Tool”
Researchers studying cybersecurity have found a malicious package on the npm package registry that poses as a library for identifying Ethereum smart contract vulnerabilities but actually installs Quasar RAT, an open-source remote access trojan, on developer PCs.
The heavily obfuscated package, named ethereumvulncontracthandler, was published to npm on December 18, 2024, by a user named “solidit-dev-416.” As of writing, it continues to be available for download. It has been downloaded 66 times to date.
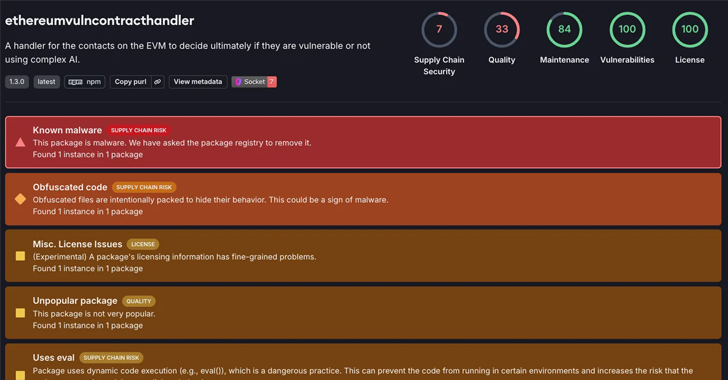
In an analysis released this month, socket security researcher Kirill Boychenko stated, “Upon installation, it gets a malicious script from a remote server, executing it silently to distribute the RAT on Windows systems.”
In order to evade analysis and detection efforts, the malicious code encoded in ethereumvulncontracthandler is hidden using several layers of obfuscation, including strategies like Base64- and XOR-encoding in addition to minification.
Before executing a second-stage payload from a distant serverIn an analysis released this month, socket security researcher Kirill Boychenko stated, “Upon installation, it gets a malicious script from a remote server, executing it silently to distribute the RAT on Windows systems.”
In order to evade analysis and detection efforts, the malicious code encoded in ethereumvulncontracthandler is hidden using several layers of obfuscation, including strategies like Base64- and XOR-encoding in addition to minification.
Before executing a second-stage payload from a distant server (“jujuju[.]lat”), the virus additionally checks to make sure it will not run in sandboxed environments. The script’s purpose is to launch Quasar RAT by executing PowerShell commands., the virus additionally checks to make sure it will not run in sandboxed environments. The script’s purpose is to launch Quasar RAT by executing PowerShell commands.
For its part, the remote access trojan contacts a command-and-control (C2) server (“captchacdn[.]com:7000”) to obtain additional instructions that enable it to collect and exfiltrate data, and it establishes persistence through changes to the Windows Registry.
Since its initial public release on GitHub in July 2014, Quasar RAT has been employed by a number of threat actors for both cybercrime and cyberespionage operations.
Boychenko stated, “If this campaign is a component of a botnet infection, the threat actor also uses this C2 server to catalog infected devices, and manage numerous compromised hosts simultaneously.”
“At this point, the threat actor has full control and surveillance over the victim’s system, which is ready for frequent check-ins and to receive updated instructions.”
The Ballooning Problem of Fake Stars on GitHub
The revelation coincides with a recent study conducted by Socket and researchers from North Carolina State University and Carnegie Mellon University that found a sharp increase in fake “stars” that are used to fictitiously boost the popularity of GitHub repositories infected with malware.
Although the situation has been there for a while, the study found that most bogus stars are used to advertise temporary malware repositories that pose as bitcoin bots, gaming hacks, and pirating software.
The “open” black market, which is promoted by GitHub star merchants such as Baddhi Shop, BuyGitHub, FollowDeh, R for Rank, and Twidium, is thought to be responsible for as many as 4.5 million “fake” stars from 1.32 million accounts and 22,915 projects, demonstrating the scope of the issue.
According to The Hacker News, 1,000 GitHub stars may be purchased for $110 at the Baddhi Shop. According to the website’s description, “Buy GitHub Followers, Stars, Forks, and Watchers to increase your repository’s legitimacy and visibility,” “Your project will attract more developers and contributors if you have real interaction!”
According to the researchers, “just a few repositories with phony star campaigns are published in package registries such as npm and PyPI.” “Even fewer are used extensively. The activity patterns of at least 60% of the accounts involved in false star campaigns are insignificant.
The findings confirm that star count alone is a poor indicator of quality or reputation and should not be utilized without additional review, as the open-source software supply chain remains a desirable target for cyberattacks.
The Microsoft-owned code hosting company told WIRED in an October 2023 statement that it has been aware of the issue for years and is actively working to eliminate bogus stars from the site.
According to the researchers, “the primary weakness of star count as a statistic is that all GitHub users’ actions have equal weight in its definition.”
Therefore, as we have demonstrated in our study, a large number of bot accounts or (perhaps poor reputation) crowdsourced individuals can readily inflate the star count. In order to prevent this kind of abuse, GitHub might think about introducing a weighted indicator of repository popularity (based on network centrality dimensions, for example), which is far more difficult to falsify.