Cybersecurity researchers from ESET on Thursday stated they took down a portion of a malware botnet comprising at the least 35,000 compromised Home windows techniques that attackers had been secretly utilizing to mine Monero cryptocurrency.
The botnet, named “VictoryGate,” has been energetic since Might 2019, with infections primarily reported in Latin America, notably Peru accounting for 90% of the compromised units.
“The principle exercise of the botnet is mining Monero cryptocurrency,” ESET stated. “The victims embrace organizations in each private and non-private sectors, together with monetary establishments.”
ESET stated it labored with dynamic DNS supplier No-IP to take down the malicious command-and-control (C2) servers and that it arrange pretend domains (aka sinkholes) to observe the botnet’s exercise.
The sinkhole knowledge reveals that between 2,000 and three,500 contaminated computer systems related to the C2 servers each day throughout February and March this yr.
Based on ESET researchers, VictoryGate propagates through detachable units corresponding to USB drives, which, when related to the sufferer machine, installs a malicious payload into the system.
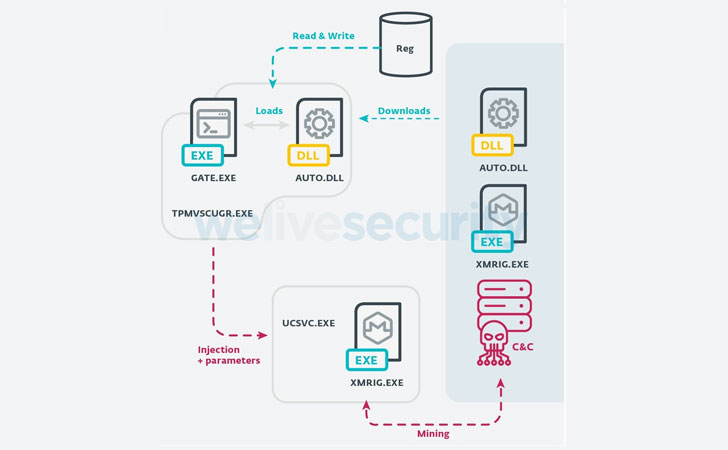
As well as, the module additionally communicates with the C2 server to obtain a secondary payload that injects arbitrary code into reliable Home windows processes, corresponding to introducing XMRig mining software program into the ucsvc.exe course of (or Boot File Servicing Utility), thus facilitating Monero mining.
“From the information collected throughout our sinkholing actions, we will decide that there are, on common, 2,000 units mining all through the day,” the researchers stated. “If we estimate a mean hash price of 150H/s, let’s imagine that the authors of this marketing campaign have collected at the least 80 Monero (roughly $6000) from this botnet alone.”
With USB drives getting used as a propagation vector, ESET warned of recent infections that would happen sooner or later. However with a big chunk of C2 infrastructure sinkholed, the bots will not obtain secondary payloads. Nevertheless, people who had been compromised earlier than the C2 servers had been taken down would nonetheless proceed to mine Monero.
“One of many fascinating traits about VictoryGate is that it reveals a larger effort to keep away from detection than earlier, related campaigns within the area,” the analysis crew concluded.
“And, given the truth that the botmaster can replace performance of the payloads which might be downloaded and executed on the contaminated units from crypto mining to another malicious actions at any given time, this poses a substantial danger.”