Researchers studying cybersecurity have discovered a new remote access virus known as NonEuclid that gives malicious actors the ability to take over infected Windows devices from a distance.
According to a technical report released last week, “The NonEuclid remote access trojan (RAT), created in C#, is a very complex virus enabling unauthorised remote access with extensive evasion strategies,” Cyfirma stated.
“It uses a number of techniques, such as ransomware encryption that targets important data, privilege escalation, antivirus bypass, and anti-detection.”
Since at least late November 2024, NonEuclid has been promoted in underground forums; talks and tutorials regarding the malware have been seen on well-known websites like YouTube and Discord. This suggests a deliberate attempt to disseminate the virus as a countermeasure against crimeware.
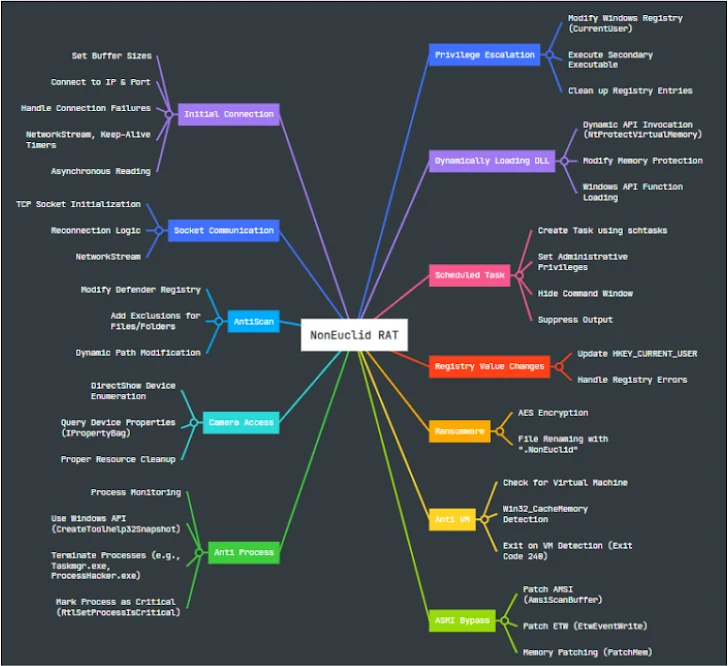
Fundamentally, the RAT starts with a client application initialization phase, then runs a number of tests to avoid detection before configuring a TCP socket to communicate with a given IP and port.
Additionally, it monitors processes like “taskmgr.exe,” “processhacker.exe,” and “procexp.exe,” which are frequently used for analysis and process management, and sets up Microsoft Defender Antivirus exclusions to stop the security tool from identifying the artifacts.
“CreateToolhelp32Snapshot, Process32First, and Process32Next are Windows API calls that are used to enumerate processes and determine whether their executable names correspond to the designated targets,” Cyfirma stated. “If a match is detected, it either kills the process or causes the client program to leave, depending on the AntiProcessMode parameter.”
The virus employs a number of anti-analysis strategies, such as detecting whether it is operating in a virtual or sandboxed environment and stopping the program right away if it is. Additionally, it has tools to get around the Windows Antimalware Scan Interface (AMSI).
NonEuclid tries to increase privileges by evading User Account Control (UAC) safeguards and executing instructions, even though persistence is achieved through scheduled operations and Windows Registry modifications.
Its capacity to encrypt files with specific extension types (such as CSV, TXT, and PHP) and rename them with the suffix “. NonEuclid,” thereby transforming them into ransomware, is a rather unusual capability.
According to Cyfirma, “The NonEuclid RAT combines sophisticated stealth techniques, anti-detection features, and ransomware capabilities, exemplifying the increasing sophistication of current malware.”
Its extensive marketing on educational platforms, Discord channels, and underground forums shows how appealing it is to cybercriminals and emphasizes how difficult it is to counter such threats. The malware’s versatility in avoiding security measures is demonstrated by the incorporation of features including privilege escalation, AMSI bypass, and process blocking.
Amidst the labyrinth of digital defense mechanisms, cybercriminals continue to forge new tools to navigate the maze undetected. In a startling revelation, cybersecurity researchers have exposed a Remote Access Trojan (RAT) named NonEuclid, which stands out for its sophisticated evasion tactics. This malicious entity has been crafted to discreetly bypass User Account Control (UAC) and slip past the keen vigilance of the Antimalware Scan Interface (AMSI). This discovery underscores a harsh reality; as cyber defenses evolve, so too does the ingenuity of cyber threats.
**Sophisticated Evasion: NonEuclid RAT**
The NonEuclid RAT is designed to infiltrate Windows systems leveraging high-level evasion techniques. RATs, known for their ability to provide administrative control over a target device, are particularly dangerous due to their stealthy nature and vast capabilities once embedded into a system.
**Bypassing User Account Control**
One of the pivotal features of NonEuclid is its ability to circumvent UAC. This security infrastructure, intrinsic to Windows since Vista, prompts users for permission before allowing programs to make changes that require administrative privileges. By exploiting design flaws or using legitimate Windows tools in unexpected ways, NonEuclid silently elevates its permissions without tripping the UAC alarms.
**Eluding Antimalware Scan Interface**
More concerning is NonEuclid’s knack for evading AMSI, a Windows feature that allows security applications to analyze potentially harmful scripts. AMSI serves to intercept scripts at runtime to scan them for threats before they execute. NonEuclid bypasses AMSI by employing various obfuscation methods or by disrupting the scanning process, rendering the malicious code invisible to security software.
**Distribution and Infection Strategies**
The distribution methods for NonEuclid are diverse, employing conventional phishing schemes, malicious attachments, and exploiting known software vulnerabilities. As the RAT finds its way into a system, it creates a backdoor for attackers, allowing them to siphon off sensitive data or take complete control over the infected machine.
**Implications for Cybersecurity Measures**
The exposure of NonEuclid throws into sharp relief the necessity for adaptive and multilayered cybersecurity measures. Traditional antivirus solutions prove insufficient against such stealthy threats, prompting the need for advanced behavioral-based detection systems and heightened security awareness among users.
**Preventive Measures and Best Practices**
Recommendations from researchers urge both organizations and individual users to adopt stricter cyber hygiene practices. This includes regular updates of software, staff training to recognize sophisticated phishing tactics, and the use of advanced antivirus and antimalware tools with heuristic analysis capabilities.
**The Road Ahead for Digital Security**
As NonEuclid exemplifies the evolution of malware, the cybersecurity community must rekindle its commitment to innovation and vigilance. Building a robust defense in depth strategy with layered security controls, zero-trust principals, and ongoing threat intelligence research is paramount to outpace the tactical advancements of such intrusive software.
In conclusion, the emergence of the NonEuclid RAT is a stark reminder of the ongoing cat-and-mouse game between cyber attackers and defenders. The discovery should serve not as a cause for panic, but as a clarion call to reinforce and rethink digital defense mechanisms, keeping pace with the ever-shifting cybersecurity landscape. It is through shared knowledge, resilience, and the relentless pursuit of security enhancements that the digital realm can remain a bastion against the relentless tide of cyber threats.